You are an essential ingredient in our ongoing effort to reduce CyberSecurity Risk
Last week, while going through my spam folder, I noticed my email address and a password that I had used in the past as the subject of a message. Curious, I decided to take a look at the email. The body of the email contained the following message, which to be honest had me laughing and worried at the same time.
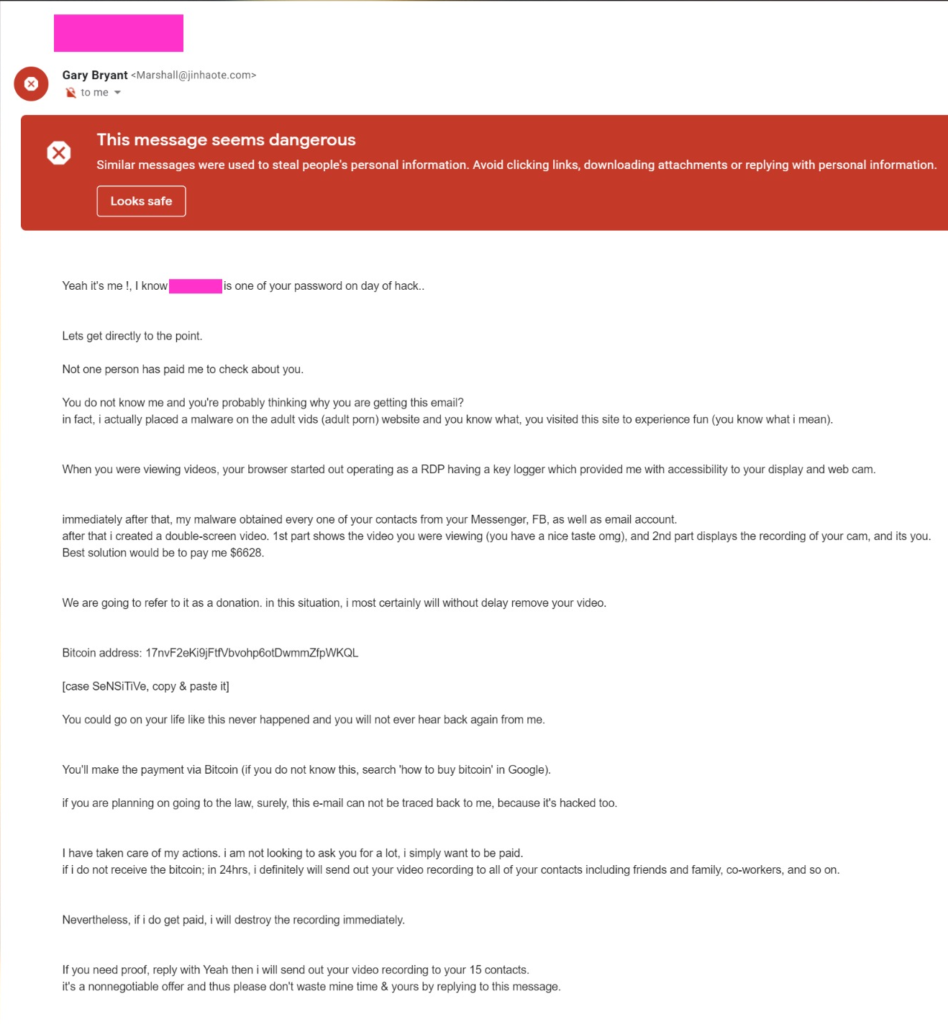
So What Exactly are Sextortion scams ?
Sextortion scams are nothing new, a sextortion or porn scam is when a scammer emails you claiming to have infected your device with malware and seen your every action online. They establish themselves as credible by adding an old password or personal information of yours in the email,
They go as far to claim that they have stolen intimate photos of you or have taken photos of you browsing online porn via your hacked webcam. They threaten to post this material online and/or send them to your friends and family, unless you pay them in bitcoins to a BTC address that they provided in the email.
Note that the type of scam I am describing is a more specific case of a social engineering attempt where the attacker is claiming to have information they don’t have to trick the victim into taking actions the attacker wants them to take.
So how do you respond to a sextortion email
- Seriously Don’t panic: Trust me the first instinct for anyone is to panic after reading such an email, but you have to understand that the scammers almost certainly don’t have any compromising footage or photos of you, they are simply trying to scare you into falling for the scam and make the payment and this is what we call social engineering attack.
- Don’t Ever Pay Them: Even if the scammers claim that any compromising material will be deleted as soon as you pay the ransom, but the likely scenario is that as soon as you make the first payment, what’s to stop them from coming back demanding a higher amount.
- Change your compromised password and never reuse old passwords If the email includes a valid password that you still currently use, you should change the password immediately, and It’s important that you create a new stronger password. And if like me, you have difficulty remembering passwords, you can look into getting a password manager. This way, you have one password to remember, and it will remember all of your passwords for you.
- Have an update antivirus that scan for malware: If you’re worried that your device may have been compromised, you should use an up to date Anti-Virus software solution to run a full system scan. This will give you peace of mind and let you know if any malware has been detected.
- Educate Yourself: There is a need for continuous security awareness training to help people whether they are in cybersecurity or not to understand the nature of the scams, spot the scams, and spot social engineering emails. There are great books such as Cyber Smart: Five Habits to Protect Your Family, Money, and Identity from Cyber Criminals that I loved reading it’s a great book and the author uses stories to help you understand a scenario, or you can also sign up for breach notifications from Fire Monitor or use a service like Have I Been Pwned.
- Set up multi-factor authentication: Multi-factor authentication is a great way to protect yourself from credential theft and today most social media platforms and other websites make use of multi-factor authentication, and they have a setup guide that’s easy to follow. It should be one of your top priorities if you are concerned about password security.
In conclusion It’s important to remember that we live in a time when password breaches are common, and too many people have been victims to this type of scams and even if they wouldn’t admit it because they might be embarrassed, I would like to make it clear that there is nothing to be embarrassed about, we live in a day and age when even the strongest security measures put in place a data breach can still happen the thing about risk is it can’t be completely eliminated, so we always have to stay vigilante.
Did you like this post?
Please let me know by leaving a comment below and tag @she_is_digital on Instagram.
Work cited
Sextortion’ scam uses password breaches to target victims. Fox News. (2021). Retrieved 14 February 2021, from https://www.foxnews.com/tech/sextortion-scam-uses-password-breaches-to-target-victims.
Sjouwerman, S. (2021).
Blackmail and Sextortion Attacks Use Panic and Threats to Lure Their Victims. Blog.knowbe4.com. Retrieved 14 February 2021, from https://blog.knowbe4.com/blackmail-and-sextortion-attacks-use-panic-and-threats-to-lure-their-victims.


Sweet blog! I found it while looking’s for ways to protect myself online, thank you so much!!